Strong Security System for
Blocking External Access
Firewall

It is a powerful security system that blocks external access by shutting down all the ports except for
the ones used to provide the services. This prevents network security incidents, blocks external threats
or illegal traffic, and allows only normal traffic.
* For details, please consult with the person in charge. Additional charges may apply depending on
the service environment or customer requirements.
 |
 |
|---|---|
| Juniper SRX Series | Cisco Firepower Series |
 |
|
| Fortinet FORTIGATE Series |
Configuration Diagram

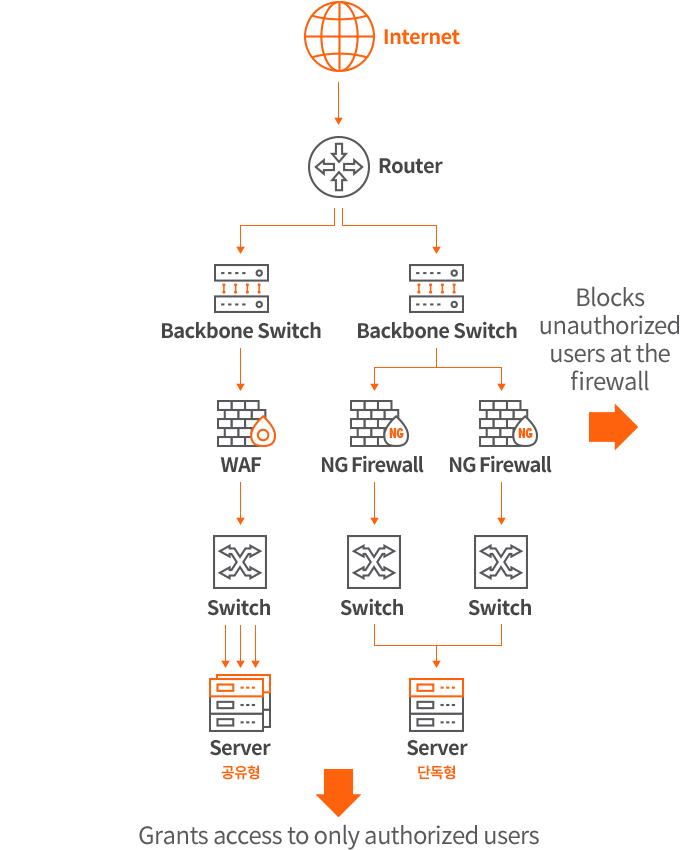
Features

| Category | Shared Firewall | Standalone Firewall |
|---|---|---|
| Bandwidth | Less than 5Mbps | 5Mbps~100Mbps |
| Firewall | Shared | Standalone |
| Port Restriction Service | Applie | Applie |
| Monitoring Service |
- Around-the-clock performance monitoring - Remote updates - Remote control of the firewall system |
|
| Real-Time Log Backup | 3 months | 3 months |
| Services Provided at Customer’s Request |
- Monthly monitoring service report - Analysis of security vulnerabilities - Security consulting |
- Monthly monitoring service report - Analysis of security vulnerabilities - Security consulting - Network impairment / performance monitoring |
• The firewall service is a type of port restriction service, and blocking of intrusion via the service ports (open ports) is not guaranteed.
• To prevent service port intrusions, you must use an additional web firewall service.
• The customer is responsible for the firewall security (rules setting, etc.) policy that they have requested.
• In the event of a problem with the security equipment (firewall), the security service may be temporarily suspended to recover and replace the security equipment.
• Monthly monitoring reports are provided in the form of a problem analysis report for the servers in which a problem occurred (upon customer request).
• This is a firewall monitoring service provided through InfoSec, an information security company.
Around-the-Clock
Monitoring Service

Even if you have excellent equipment or solutions, you won’t be able to prevent an unforeseen attack without an engineer with professional expertise and skills in this area. Our engineers will actively respond to network problems and various adverse situations and help keep your services running 24/7 without any interruptions.
| Category | Products |
|---|---|
| Integrated Event Monitoring | 2Around-the-clock monitoring for network impairments and performance |
| Around-the-clock monitoring for system impairments and performance | |
| Around-the-clock monitoring for security event | |
| Around-the-clock impairment/failure monitoring and response | |
| Proactive Response and Real-Time Response | Proactive network impairment monitoring and response |
| Response to intrusion attempts by primary and secondary response teams | |
| Consistent handling from event report from the customer to completion | |
| Operation of the CERT Team | Analysis of trends regarding new vulnerabilities reported daily from around the world |
| Real-time change analysis (threat rate), risk levels of vulnerabilities and latest analysis report | |
| Signature registration for vulnerabilities of service ports | |
| Reporting Service | Monthly service reports |
| Impairment handling reports | |
| Help Desk | Tech support for security |
| Service improvement and complaints handling |








